I wanted to write about the importance of checking for new services as this is an avenue in which attackers leverage their persistence methods.
While looking at newly created services in a Windows environment, I spotted an executable called “wsus.exe”. Now most of you might be familiar with Microsoft Windows Update Services; however, having done patch management in the past, I knew there was no such thing as “wsus.exe” on a workstation device. In addition, the file path seemed very odd to me.
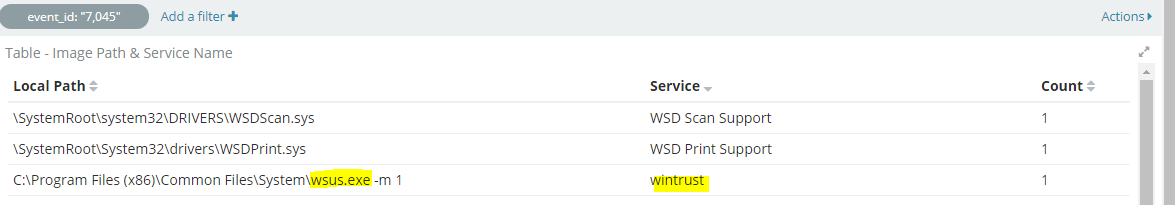
I found the file along with the file hash
SHA256: 9C2A5540B68EEBE84C446A05763869AC6BA59B76151BF697639F45C7422A8AD7
Filename: wsus.exe (original name: USD.exe)
Signed by: 1549 LIMITED
At this point I realized that this was not a file I wanted to have running on our endpoints, and at that point of time, the file was unknown to Virustotal/Hybrid-Analysis. An incident response procedure followed after this.
Another Example of a more obvious service registered are obfuscated powershell commands such as this one. This is using Psexec_psh to establish a reverse TCP connection over port 4444 using a public python script.
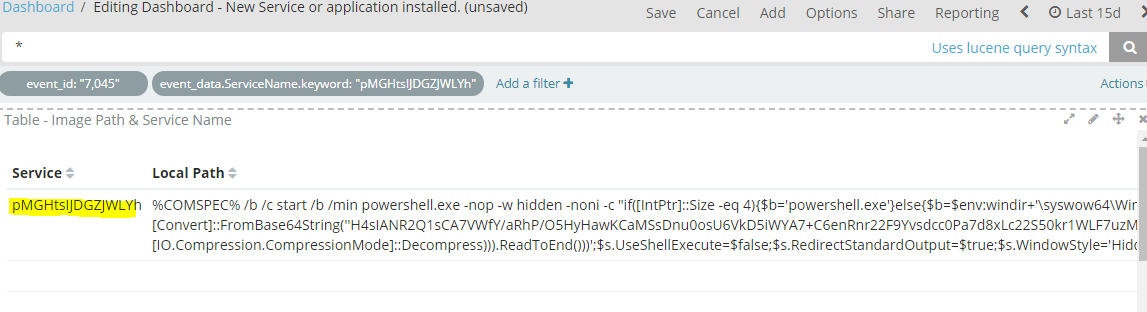
Full text:
%COMSPEC% /b /c start /b /min powershell.exe -nop -w hidden -noni -c "if([IntPtr]::Size -eq 4){$b='powershell.exe'}else{$b=$env:windir+'\syswow64\WindowsPowerShell\v1.0\powershell.exe'};$s=New-Object System.Diagnostics.ProcessStartInfo;$s.FileName=$b;$s.Arguments='-noni -nop -w hidden -c &([scriptblock]::create((New-Object IO.StreamReader(New-Object IO.Compression.GzipStream((New-Object IO.MemoryStream(,[Convert]::FromBase64String(''REALLYLOOOONGENCODEDTEXTGOESHERE''))),[IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))';$s.UseShellExecute=$false;$s.RedirectStandardOutput=$true;$s.WindowStyle='Hidden';$s.CreateNoWindow=$true;$p=[System.Diagnostics.Process]::Start($s);"
This particular registered service stands out and made it easier to detect.
Filtering out the known good
So now you might be telling yourself “I’m going to look at newly registered services, and scheduled tasks, etc.. to find unexpected services”; however, on this daily routine you will find yourself looking at the same HP Printer drivers [or insert vendor name] or other hardware drivers along with your AV protection software that will continue to get updated.
Over time I realized it was best to filter out this “noise” and only show relevant services which would easily stand out. Unfortunately using WEF, I don’t have a way to filter out these events (whether it’s by editing the xml file, etc.) so I found it easier to do it at the log parser level, therefore I created a Logstash filter.
This is a basic example of a configuration you may use to either filter out your expected logs or label them differently if still want to store them.
For this example I’m excluding Sysmon, Windows Defender, and other common applications that will be noisy for event ID 7045 which is used for newly installed services.
#Drops Common Windows Services installed
filter {
if "winlogbeat" in [tags] and [event_id] == 7045
and ([event_data][ImagePath] == "C:\Windows\SysmonDrv.sys"
or [event_data][ImagePath] == "C:\windows\SysmonDrv.sys"
or [event_data][ImagePath] == "C:\Windows\Sysmon.exe"
or [event_data][ImagePath] == "C:\windows\Sysmon.exe"
or [event_data][ImagePath] =~ /C:\\Windows\\ccmsetup\\ccmsetup.exe/
or [event_data][ImagePath] =~ /C:\\ProgramData\\Microsoft\\Microsoft Antimalware/
or [event_data][ImagePath] =~ /c:\\ProgramData\\Microsoft\\Microsoft Antimalware/
or [event_data][ImagePath] =~ /C:\\ProgramData\\Microsoft\\Windows Defender/
or [event_data][ImagePath] =~ /c:\\ProgramData\\Microsoft\\Windows Defender/
or [event_data][ImagePath] =~ /^"[a-zA-Z]:(\\[^\:\\]+)\\HP/
or [event_data][ImagePath] =~ /^"[a-zA-Z]:(\\[^\:\\]+)\\Common Files\\Adobe/
){
drop { }
}
}
As you can see you can easily paste the full path of the application and exclude them.
One of the challenges I found was registered services with with quotes “” under the full path as show in the image below:
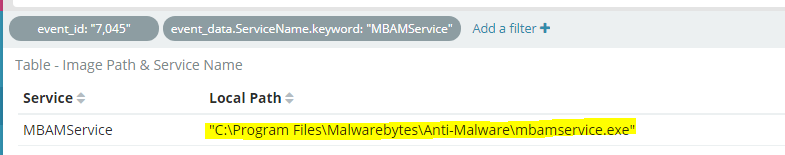
C:\Program Files\Malwarebytes\Anti-Malware\mbamservice.exe is different from “C:\Program Files\Malwarebytes\Anti-Malware\mbamservice.exe” with regards to Logstash parsing. Closing quotes in logstash are used to escape and move on to the next line. The way I dealt with this was by using regex (Using Regex101 to test my patterns).
This is the way to deal with it:
^”[a-zA-Z]:(\\[^\:\\]+)\\Malwarebytes\\Anti-Malware\\mbamservice.exe which will match “C:\Program Files\Malwarebytes\Anti-Malware\mbamservice.exe”
With regex you can either match a specific file or a folder which would cover any files within that particular path. I suggest you match the whole file path to ensure that malware hiding under a legitimate folder path doesn’t get excluded.
If you want to be fancy and ensure you’re not just filtering out a specific path, but rather the actual service name, you can also filter based on that.
Example:
Service name: MBAMService
Path: C:\Program Files\Malwarebytes\Anti-Malware\mbamservice.exe
Logstash Filter:
#This is for MalwareBytes MBAM or ([event_data][ServiceName] == "MBAMService" and ([event_data][ImagePath] == "C:\Program Files\Malwarebytes\Anti-Malware\mbamservice.exe" ))
This will ensure that you are 100% confident you are only filtering out expected registered services.
Scheduled Tasks
Another place I often find interesting items is under Scheduled Tasks
Disclaimer: Scheduled tasks is very very noisy, so heavy filtering needs to take place; however, once you are done, I can guarantee that you’ll find some interesting items (mainly Adware that your end users installed, or potentially something more serious )
Items found in the past: Mining Software, Adware Updaters, etc.
Here’s an example of a miner used to download and update .json configuration file and pool URL information.
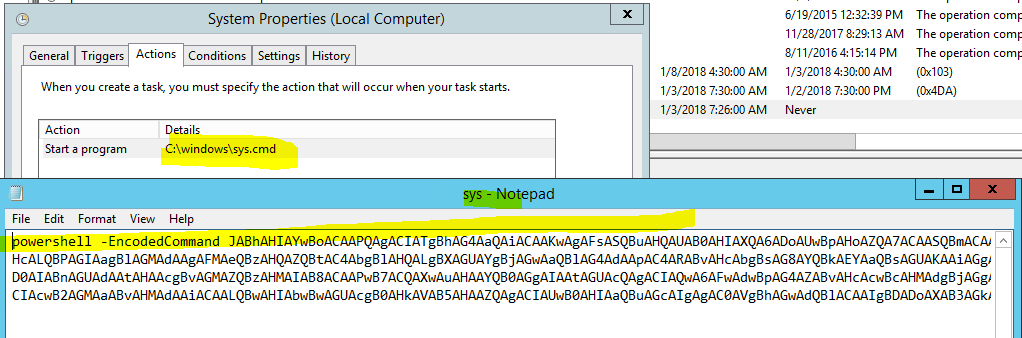
It’s easy to blend in with legitimate-sounding scheduled task names that run constantly; however, once you filter out what you know it’s expected, then you might start finding the more nefarious ones.
The most common applications that will generate the most scheduled tasks are those that you already expect such as Microsoft products, Adobe Reader, GoToMeeting,Dropbox Updates, Google Updates, etc.. Here’s a basic Logstash configuration to filter out those to help you get started. For many of these I’m leveraging the Grok Regex patterns for Logstash that makes it much simpler to filter out these logs.
You have 3 ways of filtering out these events:
Action Name: Windows Path to a particular file that is being executed
Task Name: This is simple the name of the task (It’s tempting to exclude by task name; however, malware authors might use the same task names as legitimate ones) which I would not recommend.
Path: This will also display the path to a particular file being ran.
In addition you can always combine both the Action Name & Task Name or Path with the Task Name to ensure that you are filtering out what you intended to leave out.
Below is an example of how you can filter these events.
#Drops Scheduled tasks
filter {
if "winlogbeat" in [tags] and [log_name] == "Microsoft-Windows-TaskScheduler/Operational" and ([event_data][Path] == "C:\Program Files (x86)\Google\Update\GoogleUpdate.exe"
or [event_data][Path] =~ /\\AppData\\Local\\GoToMeeting\\\d{4}/
or [event_data][Path] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\Intel/
or [event_data][Path] =~ /\\AppData\\Local\\Citrix\\GoToMeeting\\\d{4}/
or [event_data][Path] =~ /\\AppData\\Local\\Google\\Update\\GoogleUpdate.exe/
or [event_data][Path] =~ /\\AppData\\Local\\Dropbox\\Update\\DropboxUpdate.exe/
or [event_data][Path] =~ /\\AppData\\Local\\Microsoft\\OneDrive\\OneDriveStandaloneUpdater.exe/
or [event_data][Path] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\Dropbox\\Update\\DropboxUpdate.exe/
or [event_data][Path] =~ /C:\\ProgramData\\Microsoft\\Microsoft Antimalware/
or [event_data][Path] =~ /C:\\ProgramData\\Microsoft\\Windows Defender/
or [event_data][Path] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\SysWOW64\\Macromed\\Flash/
or [event_data][Path] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\SysWoW64\\Macromed\\Flash/
or [event_data][Path] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\system32\\Macromed\\Flash/
or [event_data][Path] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\HP/
or [event_data][Path] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\Hewlett-Packard/
or [event_data][Path] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\Citrix\\GoToMeeting\\\d{4}/
or [event_data][Path] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\GoToMeeting\\\d{4}/
or [event_data][Path] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\NVIDIA Corporation/
#You can also filter by Task name
or [event_data][TaskName] =~ /\\Microsoft\\Windows/
or [event_data][TaskName] == "\OfficeSoftwareProtectionPlatform\SvcRestartTask"
# Or by ActionName
or [event_data][ActionName] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\Google\\Update\\GoogleUpdate.exe/
or [event_data][ActionName] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\SysWOW64\\Macromed\\Flash/
or [event_data][ActionName] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\SysWoW64\\Macromed\\Flash/
or [event_data][ActionName] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\system32\\Macromed\\Flash/
or [event_data][ActionName] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\Bonjour/
or [event_data][ActionName] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\NVIDIA Corporation/
or [event_data][ActionName] =~ /\\AppData\\Local\\GoToMeeting\\\d{4}/
or [event_data][ActionName] =~ /\\AppData\\Local\\Citrix\\GoToMeeting\\\d{4}/
or [event_data][ActionName] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\GoToMeeting\\\d{4}/
or [event_data][ActionName] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\Citrix\\GoToMeeting\\\d{4}/
or [event_data][ActionName] =~ /\\AppData\\Local\\Google\\Update\\GoogleUpdate.exe/
or [event_data][ActionName] =~ /\\AppData\\Local\\Dropbox\\Update\\DropboxUpdate.exe/
or [event_data][ActionName] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\Dropbox\\Update\\DropboxUpdate.exe/
or [event_data][ActionName] =~ /^[a-zA-Z]:(\\[^\:\\]+)\\Common Files\\Adobe/
or [event_data][ActionName] =~ /[a-zA-Z]:(\\[^\:\\]+)\\Microsoft Office/
# Or you can also do a combination of both the task name and the actual file path to ensure you are filtering what's intended.
#This is for taskhostw.exe Scheduled Tasks
or ([event_data][Path] == "taskhostw.exe"
and ([event_data][TaskName] =~ /\\Microsoft\\Windows/ ))
#This is for taskhost.exe Scheduled Tasks
or ([event_data][Path] == "taskhost.exe"
and ([event_data][TaskName] =~ /\\Microsoft\\Windows/ ))
#This is for taskhost.exe Scheduled Tasks
or ([event_data][Path] == "taskhostex.exe"
and ([event_data][TaskName] =~ /\\Microsoft\\Windows/ ))
#This is for rundll32.exe Scheduled Tasks
or ([event_data][Path] == "%windir%\system32\rundll32.exe"
and ([event_data][TaskName] =~ /\\Microsoft\\Windows/ ))
#This is for rundll32.exe Scheduled Tasks
or ([event_data][Path] == "C:\Windows\SYSTEM32\cmd.exe"
and ([event_data][TaskName] == "Your Own custom scheduled tasks"
or [event_data][TaskName] == "Additional custom scheduled task names" ))
)){
drop { }
}
}
Hope this helps! if you have any questions, feel free to ask.
Looking for abnormal behavior
The point of this is to ensure that we’re leveraging our Analyst talents and insight to ensure that we’re catching persistent methods used by attackers, whether it’s by looking at newly installed services, registry writes, or scheduled tasks.
I would suggest any reader to familiarize themselves with the Mitre ATT&CK Framework if you’re not already doing it. This will allow any team to have a framework to follow in order to ensure that we have full coverage of various forms of attacks.
Mitre ATT&CK Framework
What is MITRE? You can read my thesis in which I talk more about it, but here’s a summary:
MITRE, a non-profit that operates research and development centers for the federal government
designed The Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) model &
framework. The ATT&CK provides a repository of adversary tactics and techniques observed on
past incidents against organizations. The incident data relied heavily on publicly available threat
reports and threat intelligence offerings such as those from Mandiant’s APT report
Mitre ATT&Ck Tactics for this particular post:
Tactic: Persistence
Technique ID: T1050
Name: New Service
Related Event IDs: 7045
Technique ID: T1053
Name: Scheduled Task
Related Event IDS:
| Task | EventID |
| Task Started | 100 |
| Task registration updated | 140 |
| Action started | 200 |
| Created Task Process | 129 |
| Task registered | 106 |
| Task registration deleted | 141 |
Thanks for reading!