After seeing a vast amount of phishing emails coming through, I’ve decided to implement an additional protection by tagging possible phishing emails by applying my own set of conditions to look for specific email subjects.
Doing a 3-5 month email search on our data collected from exchange, I looked at multiple common subject emails used by phishing campaigns and were able to differentiate legitimate email senders from other phishing emails used for these campaigns.
A legitimate Dropbox email will contain the subject line “Full Name shared “Filename” with you”, and similar subjects will be used by OneDrive, and other legitimate services. Phishing campaigns will attempt to blend in by using similar subject lines along with company logs to create trust.
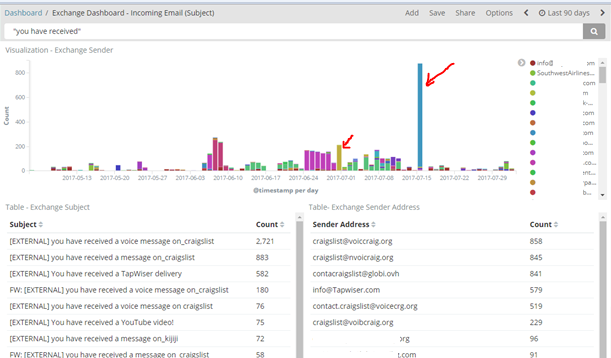
In the figure above, you can see the reoccurring senders (which are those that might be trusted), vs the ones that spike only once or twice in a period of 3 months. Using this data I created a whitelist sender lists for those that we potentially do business with.
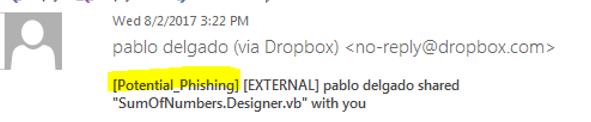
Emails containing specific subjects that are NOT coming from trusted senders will get a [Potential_Phishing] tag added (see image below)
How do we accomplish this with Proofpoint?
A new policy was created on proof point called “pp_PotentialPhishSubjectTag” (Email Protection > Rules)
Which does the following:
![]()
- If the email subject contains the words “has shared with you”, OR if the subject line contains a set list of “Dictionary words” (This will be explained later), then it will add the subject tag [Potential_Phishing].
- The tag will NOT be added if the sender is part of another Policy Routes (System > Policy Routes “Excludes_Potential_Phishing”) list. This list contains the whitelisted domains or email addresses.
The following will explain the components of the overall policy:
Dictionary words: Dictionary words may be used to create a list of words to be used for custom policies that you might have. In our use case, we want to add possible subject lines that match incoming emails.
Located in Email Protection > Dictionaries.
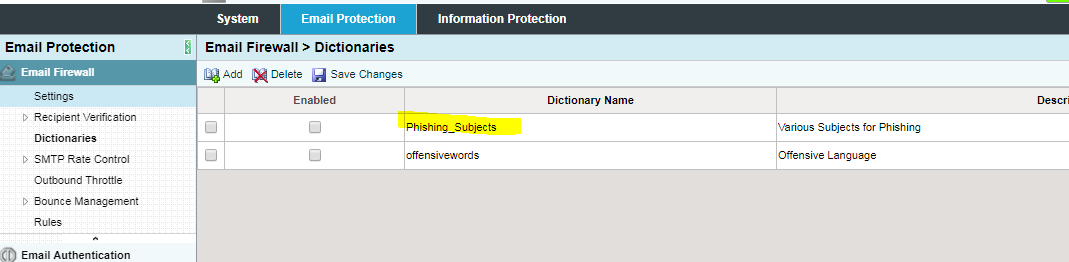
You may click on Phishing_Subjects and add additional subjects that match potential phishing emails here.
Note: dictionaries are only good if you have full matching text, otherwise you will have to do a regex.
An example that will work: Email subject contains: hey! you have received a new document in dropbox!
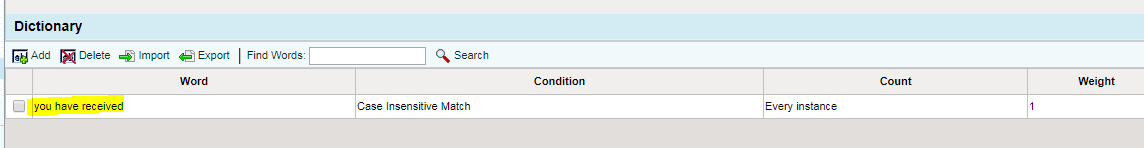
The dictionary word “you have received” would match our condition and our policy would apply.
To add new dictionary words navigate to: Email Protection > Dictionaries > Add.
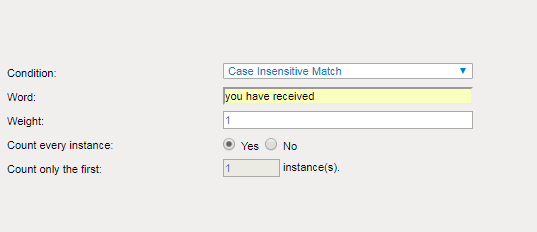
Ensure that you add a weight of “1”.
Now, an example that will NOT work: Email subject contains: Hey! You have a new items waiting to be received.
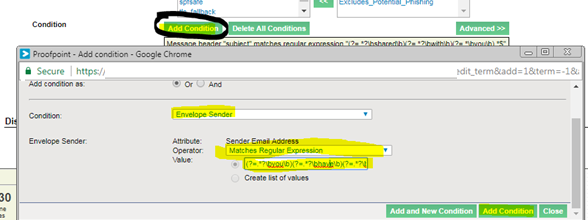
For this, you would have to create a regex rule: (?=.*?\byou\b)(?=.*?\bhave\b)(?=.*?\breceived\b).*$
This will trigger a match when a subject contains those three words (It will not trigger if there’s only one or two words out of the 3).
To add the regex, navigate to (Email Protection > Rules > “pp_PotentialPhishSubjec_tag” > Edit Rule
– Add condition
-Envelope Sender
-Matches Regular expression: Paste your values there.
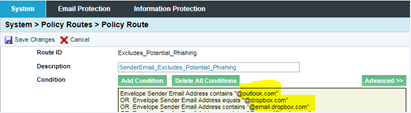
Adding Trusted email senders: System > Policy Routes > “Excludes_Potential_Phishing”
- Add conditions
- Add condition as “OR”
- Condition: Envelope Sender
- Operator: (Either Contains, or Equals if you have an exact email address)
- Value: email address
I’m sure you can accomplish something similar with your current email gateway solution or Office 365.
Optional: Moving tagged emails to Junk mail via Outlook
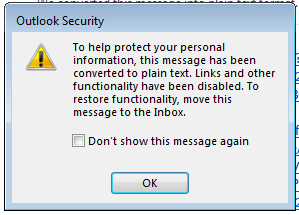
An exchange rule will automatically place these emails in the user’s Junk E-mail folder. Emails within the user’s Junk E-mail will not work unless they are moved to the user’s inbox. (They will see the message below if try attempt to click on a link within the Junk folder).
Depending on your version of Exchange, you may do the following:
When Subject Field contains: Potential_Phishing
Set Spam confidence level to 6,
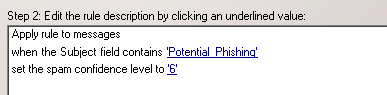
This will ensure that the email goes directly to the Junk Inbox so the user may not automatically click on any potential malicious links.
Fast Forward 6 Months later:
I implemented this since last year, and as you can see, this rule is still catching many phishing campaigns.
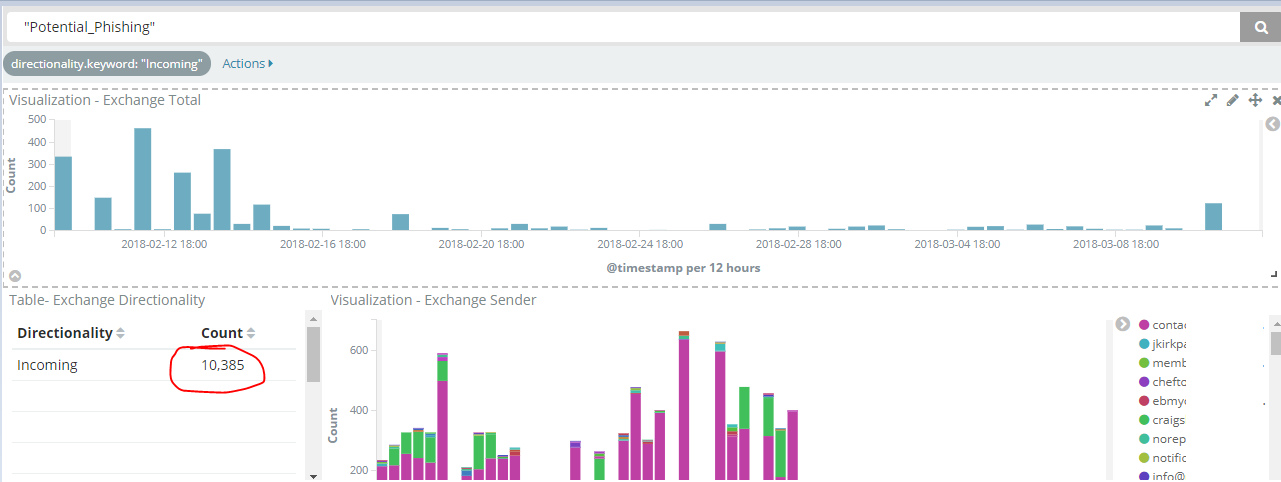
This goes to show that manual regex rules and common sense will stop many of these phishing campaigns that might easily get past your email security.
That’s all. I hope you got some new ideas regarding emails. Remember that you may implement this with your existing security products or with Microsoft Exchange. The tricky part is ensuring that you are 100% sure that you can identify the hostname sending these emails as email spoofing is very simple. If you rely on display name for email rules you are not doing it right.
Thank you!